Security is our top priority
At JET, we take security very seriously. As your trusted supplier, we are committed to upholding the highest security standards. We do this by adhering to strict security regulations and obtaining the necessary accreditations, ensuring your data and operations are always protected.


Security is our top priority
At JET, we take security very seriously. As your trusted supplier, we are committed to upholding the highest security standards. We do this by adhering to strict security regulations and obtaining the necessary accreditations, ensuring your data and operations are always protected.
Browse by Topic
Our Security Standards
We are proud to say that we uphold the following security standards:
✔ ISO 27001
We are ISO 27001 certified, meaning we uphold the international standard for managing information security
✔ PCI 4.0
✔ Cyber Essentials Certified Plus
✔ GDPR Compliant
Our Security Policies
We have implemented and continue to manage a comprehensive range of security policies governed by our parent company, Vesta Software Group, and overseen by our team here at JET.
Vesta Software Group Policies
✔ General Information Security Policy
✔ User Access Policy / Acceptable Use Policy
✔ Password Policy
Jonas Event Technology Policies
✔ Business Continuity Plan
✔ Disaster Recovery Plan
✔ Data Backup and Recovery Policy
✔ Logical Access Control Policy
✔ Change Management Process
✔ Risk Management Process
Network Security
When it comes to network security, we have implemented a comprehensive set of measures, including:
✔ Firewalls
✔ Web Application Firewall (WAF/CloudFlare)
✔ Anti-DDoS (CloudFlare)
✔ Intrusion Detection System
✔ JET back-office access is secured through a VPN with multi-factor authentication, available only to need-to-know staff.
✔ Encrypted communications (HTTPS)
Operational Security
For operational security, our R&D team ensures smooth and effective operations by:
✔ Performing monthly patch management as a standard practice
✔ Regularly reviewing data backups
✔ Forwarding all platform logs to a Security Information and Event Management (SIEM) solution
✔ Conducting quarterly and annual reviews of our security policies and management processes
Business Continuity and System Resilience
✔ Our infrastructure has separate layers for internal, test, and production systems as well as front-end and back-end databases.
✔ We have separate data centres for production and disaster recovery to ensure reliability.
✔ Our systems are designed to handle more capacity than needed, even during peak times
✔ We have incorporated a load management system to prevent overload
✔ Content delivery is optimised with CloudFlare caching for better performance.
✔ We have a fully functional disaster recovery setup for emergencies.
✔ Our tier 1 data centres are highly secure and ISO 27001 certified.
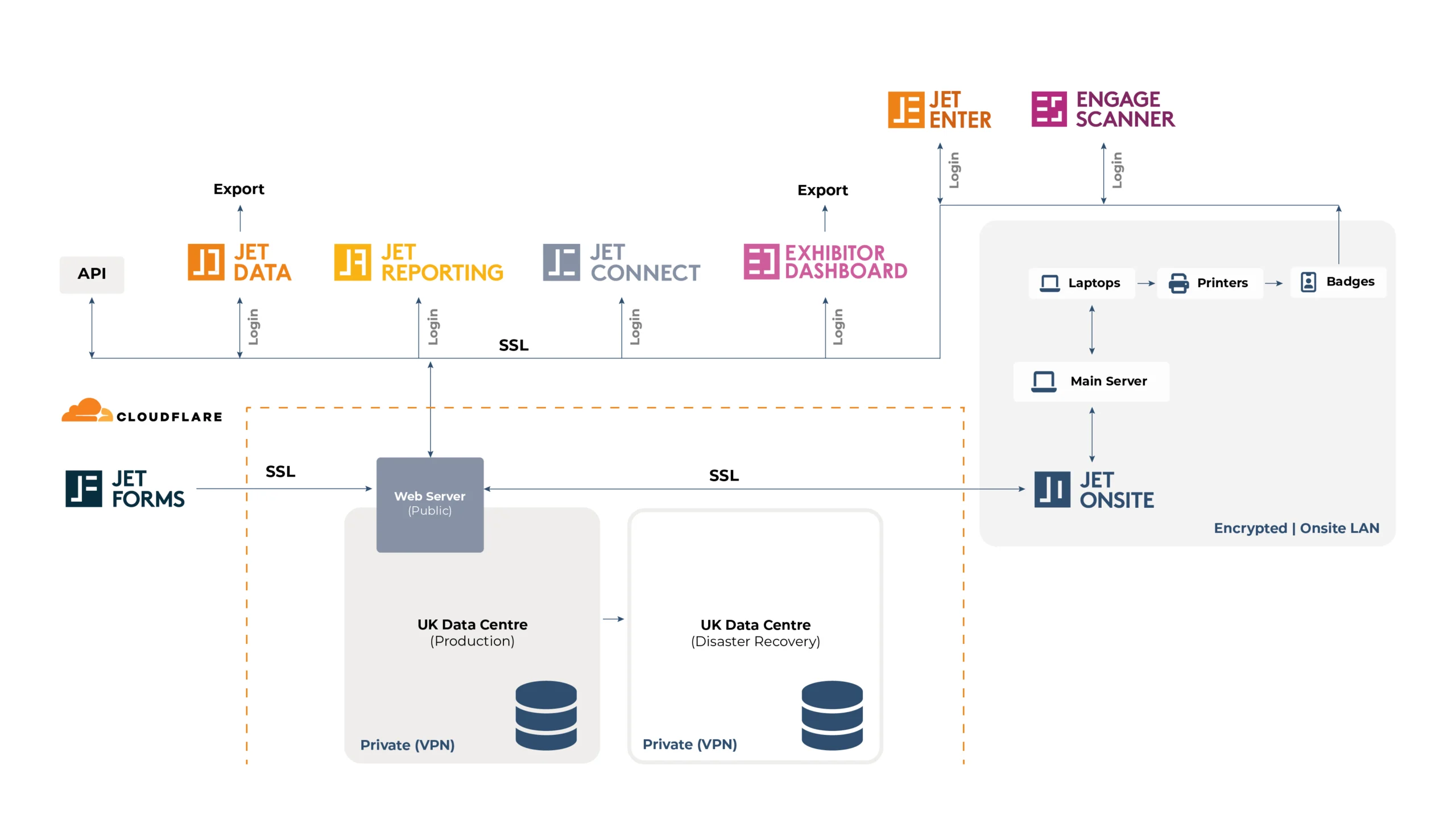
Data Flow
How data flows through our system:
Browse by Topic
Our Security Standards
We are proud to say that we uphold the following security standards:
✔ ISO 27001
We are ISO 27001 certified, meaning we uphold the international standard for managing information security
✔ PCI 4.0
✔ Cyber Essentials Certified Plus
✔ GDPR Compliant
Our Security Policies
We have implemented and continue to manage a comprehensive range of security policies governed by our parent company, Vesta Software Group, and overseen by our team here at JET.
Vesta Software Group Policies
✔ General Information Security Policy
✔ User Access Policy / Acceptable Use Policy
✔ Password Policy
Jonas Event Technology Policies
✔ Business Continuity Plan
✔ Disaster Recovery Plan
✔ Data Backup and Recovery Policy
✔ Logical Access Control Policy
✔ Change Management Process
✔ Risk Management Process
Our Security Policies
We have implemented and continue to manage a comprehensive range of security policies governed by our parent company, Vesta Software Group, and overseen by our team here at JET.
Vesta Software Group Policies
✔ General Information Security Policy
✔ User Access Policy / Acceptable Use Policy
✔ Password Policy
Jonas Event Technology Policies
✔ Business Continuity Plan
✔ Disaster Recovery Plan
✔ Data Backup and Recovery Policy
✔ Logical Access Control Policy
✔ Change Management Process
✔ Risk Management Process
Network Security
When it comes to network security, we have implemented a comprehensive set of measures, including:
✔ Firewalls
✔ Web Application Firewall (WAF/CloudFlare)
✔ Anti-DDoS (CloudFlare)
✔ Intrusion Detection System
✔ JET back-office access is secured through a VPN with multi-factor authentication, available only to need-to-know staff.
✔ Encrypted communications (HTTPS)
Operational Security
For operational security, our R&D team ensures smooth and effective operations by:
✔ Performing monthly patch management as a standard practice
✔ Regularly reviewing data backups
✔ Forwarding all platform logs to a Security Information and Event Management (SIEM) solution
✔ Conducting quarterly and annual reviews of our security policies and management processes
Business Continuity and System Resilience
✔ Our infrastructure has separate layers for internal, test, and production systems as well as front-end and back-end databases.
✔ We have separate data centres for production and disaster recovery to ensure reliability.
✔ Our systems are designed to handle more capacity than needed, even during peak times
✔ We have incorporated a load management system to prevent overload
✔ Content delivery is optimised with CloudFlare caching for better performance.
✔ We have a fully functional disaster recovery setup for emergencies.
✔ Our tier 1 data centres are highly secure and ISO 27001 certified.
Data Flow
How data flows through our system: